131 - Boot to a TrueCrypted Win 8.1 hard disk via USB
Add a Comment about this article
Introduction
This Tutorial describes how you can protect your TrueCrypt encrypted PC by only being able to boot it from your USB drive. Anyone who switches on your PC will just be greeted with a blank screen or the PC may just reboot. The Windows partition will appear as unformatted if anyone boots from another USB drive or CD/DVD.
Note: In the text below TC = TrueCrypt.
To boot from the PC (any partition) you will need to do the following:
Insert you USB drive
MBR-boot from your USB drive to a grub4dos menu
Choose the menu entry to boot to the TrueCrypt password screen
Enter you TC password and it will boot
Note that with this method you do not have to save an MBR or other sectors to a file.
Note: TrueCrypt development has now been discontinued and it is recommended not to use it (see here). You can use VeraCrypt instead.
Prerequisites
Window should boot in MBR mode (not UEFI) and the partitions should be the old-style MBR partitions (not GPT partitions) - TC does not support UEFI anyway, so thus should not be a problem!
You will need a USB drive of any size, which has grub4dos installed (use a 2015 version if possible)
Easy2Boot 1.62 contains a sample TrueCrypt_USB_Boot_Only.mnu menu file which you can use (just copy it to the \_ISO\MAINMENU folder).
Windows 8.1 installation
When installing Windows, boot in MBR mode not UEFI mode
When you get to the Install menu - choose Custom (Advanced) Install and delete all partitions on the target Internal hard disk - then create a new single NTFS partition (large enough for your Windows files). You can create more partitions if you wish.
Windows 8 may warn you that it is going to create a small (200-350MB) system partition - if it does create one, just delete it if you can, using the Del 'link' provided. You may need to boot to WinPE or linux in order to erase any existing Windows partition if Windows Setup won't allow you to delete an existing Windows system partition. I have also tested with a 350MB system partition and it booted fine except that you cannot use the WinPE Recovery environment as the encrypted volumes will appear as if they are unformatted. Therefore you cannot restore an earlier backup or perform any recovery action. So, if possible, I recommend making sure that your Primary partitions are already present before you proceed with the Install.
Now continue with the installation of Windows until you get to the Desktop after 3 reboots.
Installing TrueCrypt
I downloaded TrueCrypt Setup 7.1a.exe (CRC-32: 1b1ac848, MD5: 7a23ac83a0856c352025a6f7c9cc1526, SHA-1: 7689d038c76bd1df695d295c026961e50e4a62ea)
I tested with both Win 8.1 32-bit and 64-bit which I installed using Easy2Boot directly from a Windows Enterprise 8.1 90-day evaluation ISO to a VBox VM:
Install and start TrueCrypt and click the System tab at the top of the form.
On the first screen of the wizard, select "Encrypt System Partition/Drive."
On the next screen, choose "Normal." If you want to create a hidden operating system (to further obscure your data), read more about how it works here. We won't cover it in this tutorial.
Next, choose "Encrypt the Whole Drive." This should work for most people, though if you have other partitions on your drive that you don't want encrypted, you may want to choose the Volume option instead.
When asked to encrypt the Host Protected Area, choose No, unless you have any specific reason to.
If you only have one operating system installed on your computer, choose "Single-Boot" at this next prompt. If you aren't sure, you're probably using a single-boot setup. If you're dual booting (say, with Linux or another version of Windows), choose "Multi-Boot." Both seemed to work with just a single Windows 8.1 install present..
Choose your encryption algorithm on the next screen. AES should be fine for most users.
Choose a password to protect your files. Remember, the stronger your password, the safer your files will be. Make sure you remember your password, because if you lose it, your computer will be unbootable and your data will be lost.
On the next screen, follow the instructions and move your mouse around randomly for a bit. This will ensure TrueCrypt's generates a strong, random key. Then click Next to continue with the wizard.
Next, select a location for a TrueCrypt Rescue Disk, which will help you save your data if the bootloader, master key, or other important data gets corrupted. Give it a file name and save it.
Once you've saved the file (in ISO format), you'll have the option to burn it to a TC Rescue CD or DVD. Do have to do this (using either Windows' built-in tools or a program like ImgBurn) before you can continue. Click Next when you've finished burning the disc (and keep the disc in a safe place!).
Tip: If you don't want to do this and you are using Win8/8.1 - just find the ISO file that is created in the Documents folder and double-click on it to Mount it as a drive (or use some other software like ImDisk) - this will mount the ISO and allow you to get you past this stage without needing to actually burn a CD! You should copy the ISO to a USB drive and a 'cloud' drive for safe keeping before you reboot.
Choose a Wipe Mode for your data. "None" is the fastest and best (unless you are paranoid!)
Run the System Encryption Pretest on the next screen. You'll need to restart your computer and enter your new TrueCrypt password when prompted.
If the test runs successfully, you'll get the option to begin encrypting your drive. Click on Encrypt and let it run — it'll probably take awhile (especially if you have a large drive).
Note that if you are in a hurry to test this Tutorial out, you don't need to wait for encryption to complete. Just shutdown the TC system and carry on to the next bit..
Make a grub4dos USB bootable drive
1. Use RMPrepUSB to make a bootable USB drive and install grub4dos onto it. Make sure the \grldr file is present on the USB drive and is dated at least late 2014\2015 if you are using your own USB/grub4dos drive.
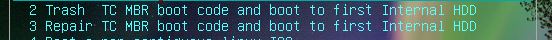
2. Now add a \menu.lst file to it containing the following menu:
title Trash TC MBR boot code and boot to first Internal HDD\n Modifies TrueCrypt boot code in MBR so it won't boot without booting from USB first
# trash boot code in MBR if still TC code
echo
cat --locate=\xea\x1e\x7c --replace=\xc3 --length=3 (hd1)0+1 > nul && echo TC Boot sector trashed!
# copy code in MBR to memory
dd if=(hd1)0+1 of=(md)0x300+1 > nul
# repair MBR boor code in memory
cat --locate=\xc3\x1e --replace=\xea\x1e --length=3 (md)0x300+1 > nul
# map hd1 (internal hdd) to hd0
map (hd1) (hd0) > nul
# chainload patched (good) MBR
chainloader (md)0x300+1
echo hd1 MBR code:
cat --hex --length=16 (hd1)0+1
echo Patched MBR code in memory:
cat --hex --length=16 (md)0x300+1
echo
set ask=
set /p:3 ask=Press R quickly to reboot!...
if /i "%ask%"=="R" reboot
boot
iftitle [cat --locate=\xc3\x1e\x7c --length=3 (hd1)0+1 > nul] Repair TC MBR boot code and boot to first Internal HDD\n Fix boot code in MBR so we can boot directly from hard disk again
# menu only shown if MBR is patched
echo
# repair byte in MBR
cat --locate=\xc3\x1e\x7c --replace=\xea --length=3 (hd1)0+1 > nul && echo TC MBR Boot sector repaired!
# make internal HDD hd0
map (hd1) (hd0) > nul
# load repaired TC MBR
chainloader (hd1)0+1
echo
echo hd1 MBR code now:
cat --hex --length=16 (hd1)0+1
echo
set ask=
set /p:3 ask=Press R quickly to reboot!...
if /i "%ask%"=="R" reboot
boot
Note that these two menus can be simplified by deleting the green lines of text, which are not needed and are just for informational/diagnostic purposes.
3. Test that the USB drive boots OK using RMPrepUSB - QEMU and then test it again by booting from the USB drive on your TC Windows system.
Disable HDD booting
To 'nadger' (technical term meaning 'trash' or 'break') the internal hard disk boot code, we just run the first menu item. This will make the whole drive unbootable just by 'patching' one single byte in the MBR on the internal hard drive. It will still boot to the TC password prompt when booting via the grub4dos menu, we can then enter our TC password and then proceed to boot to TC Windows.
Enable HDD booting
If you want to unpatch the MBR so that anyone can boot your system to the TC password prompt, just run the second menu item.
Password protect the grub4dos menu
Under each menu, you can add a grub4dos password line - e.g.
title Trash TC MBR boot code and boot to first Internal HDD\n Modifies TrueCrypt boot code in MBR so it won't boot without booting from USB first
password hereismypassword || reboot
(rest of menu here)
This will prompt the user for a password (e.g. 'hereismypassword') before it will allow you to run the menu entry and boot or restore the TC MBR. If the password is incorrect it will reboot the system.
How it works
During testing, I found that TC 7.1a did not like changes to the MBR partition table. The partition has to be marked as Active and the partition entries need to be the same as before.
The menu works by changing the first byte in the MBR boot code to a RET (return) instruction (C3h) - this essentially 'crashes' the PC when it tries to boot.
The comments in the menu should explain what each line is doing.
It is possible to destroy more of the MBR code or replace it with the standard Windows MBR code. This will disguise it even more from prying eyes!
We can wipe out all the TC MBR boot code before booting:
1. Create a file full of 00's on the USB drive using the Windows fsutil command:
fsutil file createnew e:\440zeros.bin 440
2. Make a backup of the TrueCrypt MBR before you destroy it using RMPrepUSB - Drive->File - file=E:\LBA0TC.bin, start=0, length=1SEC, files start=0 OR use BootIce. You can still use the Rescue ISO to repair the MBR or boot to the TC password prompt, so don't worry if you didn't make a backup.
3. Add this grub4dos menu to your grub4dos-bootable USB drive
title TC boot (and erase MBR code)
# erase TC MBR boot code if not already erased
cat --locate=\xea\x1e\x7c --length=3 (hd1)0+1 > nul || dd if=()/440zeros.bin of=(hd1)0+1 > nul && pause TC MBR boot code now erased on first hard disk!
# change device number
map (hd1) (hd0)
# boot from the truecrypt MBR
chainloader /LBA0TC.bin
Note that you will need the LBA0TC.bin file, so make a backup somewhere (not on the TC system!). The LBA0TC.bin file is NOT unique however, so it is no great shakes if you lose the USB drive.
You can always boot using the TC ISO file that is generated during the encryption process. You can add this ISO file to your E2B USB drive and, you can either boot directly to the TC hard disk password prompt, or Repair the 'broken' TC MBR so that you can boot directly from the TC hard disk again.
